How To Secure Data Efficiently
Categories:
[Technology]
Tags:
[security],
[privacy],
[encryption],
[open-source],
[apps]
Securing our data is the most important thing we can do in this digital age. However using PGP based products does not come easy for most.
What is PGP, GPG, and Open PGP?
PGP
PGP stands for 'Pretty Good Privacy' and rightfully so, it's pretty darn good! It is used to encrypt messages and files on your computer to be sent to another user securely and privately. This can also be used to sign a file or message so that anyone who has the file can verify that it is from you.
PGP uses a combination of hashing, data compression, symmetric-key cryptography, and public-key cryptography. We have talked about hashing and cryptography in episode 009 of the Hacker Culture podcast.
Public keys are connected to a name or email address and in most cases both. You can find keys linked to address in online databases like the one at the MIT PGP Key Server. A user can verify that the key does belong to the stated used in what is called the web of trust. Keybase takes this web of trust one step further which we'll get into shortly.
Open PGP
Open PGP is the open source version of PGP. This was created by Philip Zimmermann, the same who created PGP. He made an open source version because he knew the impact that PGP could have on the world and an open standard version would only help the cryptographic community.
GPG
GPG stands for "GNU Privacy Guard" and is another open source version of PGP that complies with the GPL. Created by Werner Koch in 1999 to work with PGP and Open PGP. GPG follows the standards set in place by Open PGP and is often included by default on Linux operating systems.
What do you use?
There are many programs out there using the open source versions of PGP since PGP is actually owned by Symantec and can't be used without paying the said company. Windows, Mac OS, and Linux all have programs designed to make it easier to use this encryption method. Command line versions are also available; I've only ever used the CLI version of GPG and the Keybase web app (when I don't have access to my Linux CLI).
What is Keybase?
Keybase is a PGP key directory at it's most basic level. What is really cool about Keybase and what sets it apart from any other PGP key directory is the social media mapping. You can verify that you are the same person on each social media site. From Facebook to Twitter to Reddit and GitHub! You can even prove that you own a particular website and post your public keys to your Bitcoin and zCash wallets.
There is also a social media aspect to Keybase itself. You can choose to follow any particular profile, and by doing so, you are contributing to the Web Of Trust as briefly mentioned above. By following an account on Keybase, you are in a sense saying, "yes this person is who they say they are and I back this." Before Keybase we would need to meet face to face, show an ID, check that emails are correct, then go home and use our PGP/GPG keys to verify that the person claiming to be XYZ in the PGP database is indeed the person it says.
Keybase also has encrypted file storage that can be shared with any of your contacts within Keybase. This function is available on the desktop computer app and mobile. Other cool features include PGP encrypted chat between you and another Keybase user or a group. They have also implemented a team feature that acts like Slack and encrypted Git for all your top secret projects.
Here is what Keybase says on their homepage:
Keybase is a new and free security app for mobile phones and computers. For the geeks among us: it's open source and powered by public-key cryptography.
Keybase is for anyone. Imagine a Slack for the whole world, except end-to-end encrypted across all your devices. Or a Team Dropbox where the server can't leak your files or be hacked.
Using Keybase
We'll focus on the web app in this section. Once you head over to Keybase.io and get the app on mobile or computer, you will be walked through the steps of setting up your account and will be assigned a PGP keypair. Then you will be able to login to the web app and do some cool stuff right in your browser.
Remember, always assume your computer is compromised and take steps to be safe out there <3
The following activities that you can do online can only be done if you do not export your keypair from Keybase and then delete them from Keybase. I have exported my keypair so I could use the same PGP identity on my mobile phone and with GPG on my desktop. I'm a nerd and like to keep my options open. If you are concerned about your keypair being leaked from the Keybase servers, you should export and delete delete from their servers, just remember that the web functionality will be lost and you'll have to follow, unfollow, sign, verify, encrypt, and decrypt manually on your computer.
Here is the top header you will see after logging into Keybase:

On the right-hand side, we see the profile image, clicking this will take you to your profile. There you will see all the social connections you made, your PGP fingerprint, who you follow and who follows you on Keybase. From this page, you can also export, delete, or get a new PGP key pair, as well as access your account settings.
The little lock next to the profile image takes to us the encrypting page. If your keys are on Keybase, you can encrypt messages (not files) by telling Keybase which user you want to encrypt the message for and whether or not you want to sign the message. Signing a message will let the person know that it is from you as you claim. This is all done by using your Keybase password you made using Bitwarden or diceware.
DO NOT USE THIS PASSWORD ANYWHERE ELSE!
Ok, good :D
This needs to be unique, so you have less of a chance of someone gaining access to your keys and sending messages as you.
You can also decrypt any messages with Keybase that are encrypted with your public key. You can choose to sign and not encrypt as well. This will keep the message in plain text for anyone to read but they will be able to check the signature and be sure that you are indeed the person who sent the message. Also, you can verify any signed message that comes your way using the 'verify' button.
After the check mark (verify) you have a little power logo, and that is to log out. Next, to that, you have the question mark, and this is where you find all the documentation for using Keybase to the fullest.
Keybase Apps
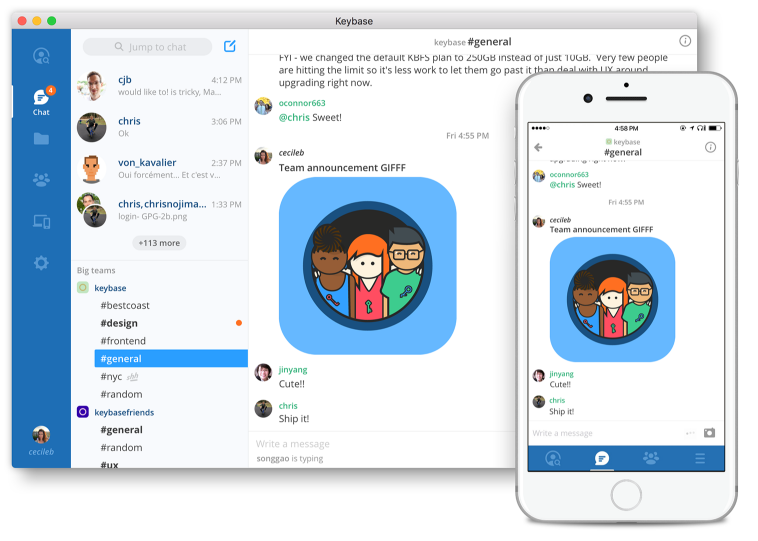
Both of the apps, desktop/laptop, and mobile, have a built-in encrypted chat in DM or team form. They also have the encrypted file sharing option, like a super secure Dropbox or Google drive. These are things that can not be done online, so if you want to use the chat or file sharing features of Keybase, you need one of the applications.
Oh, did I let you know it's open source and free! No? woops...
Keybase Commandline
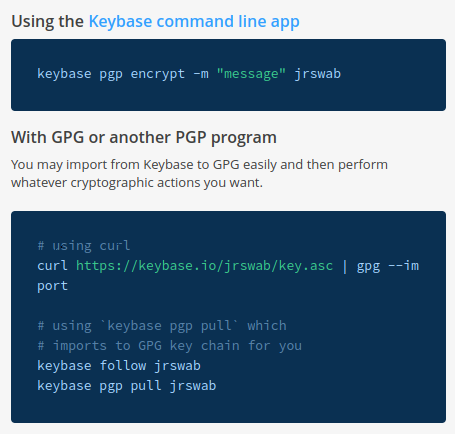
To use the command line features you will have to download and install the application on your computer. I'm not sure why you can't just download the CLI, but they chose to bundle them, so that's what we get.
You can use Keybase from the command line to follow, unfollow, and do your standard PGP/GPG stuff. I've not used these features since I have the app itself downloaded onto my PC. The documentation covers it very well so you should not have trouble finding what you need if you wish to use Keybase via command line.
If you are an email kind of nerd you can sign up for mine here. You can always replay to any of my emails to start a conversation or ask me a question. You can donate to this site from my Liberapay account if you so choose.